Dear customer,
As you know, the widespread use of e-mail has led to the proliferation of a large number of Identity Impersonation Post (PHISING) that circulate continuously over the Internet. Phishing messages try to impersonate the identity of a reliable entity, to distribute misleading information, requesting confidential data and passwords from users or sometimes try to encrypt the data of the recipients' computers to extort later if they want to restore such data.
- Dear customer,
As you know, the widespread use of e-mail has led to the proliferation of a large number of Identity Impersonation Post (PHISING) that circulate continuously over the Internet. Phishing messages try to impersonate the identity of a reliable entity, to distribute misleading information, requesting confidential data and passwords from users or sometimes try to encrypt the data of the recipients' computers to extort later if they want to restore such data. We often see cases of this type in the media. - Dear customers: After 22 years on the market, the unidirectional progressive safety gear PR-2500 will be withdrawn from our product catalogue from September 1, 2018. However, Dynatech will continue to ensure the supply of spare parts for this safety gear. The more advanced range of unidirectional ASG safety gears offer much more versatility and capacity, effectively rendering the PR-2500 obsolete. Dynatech will no longer accept orders for this product after July 31, 2018. Sincerely,
- Dear customers:
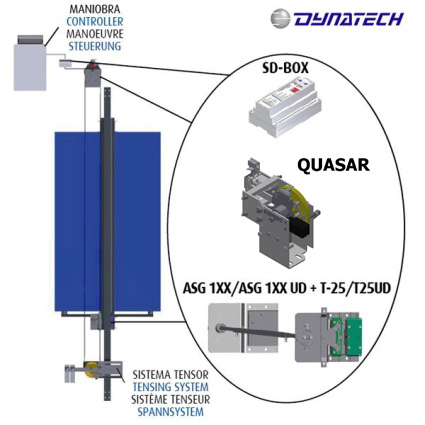
After 22 years on the market, the unidirectional progressive safety gear PR-2500 will be withdrawn from our product catalogue from September 1, 2018. However, Dynatech will continue to ensure the supply of spare parts for this safety gear.
The more advanced range of unidirectional ASG safety gears offer much more versatility and capacity, effectively rendering the PR-2500 obsolete.
Dynatech will no longer accept orders for this product after July 31, 2018.
Sincerely, - Please be informed that our summer working hours will be from 7am to 3pm between Jun 4 and August 31.
Also, the Dynatech offices will be closed for the summer holidays from 13 - 17 August inclusive.
We apologise for any inconvenience this may cause.